Bugku密码学题目writeup
滴答~滴
1 | -... -.- -.-. - ..-. -- .. ... -.-. |
答案格式KEY{xxxxxxxxx}
摩斯电码
BKCTFMISC
聪明的小羊
一只小羊翻过了2个栅栏
KYsd3js2E{a2jda}
栅栏密码
KYsd3js2
E{a2jda}
ok
在以下网址中解密
https://www.splitbrain.org/services/ook
这不是摩斯密码
下载看看吧
1.txt的内容
1 | +++++ +++++ [->++ +++++ +++<] >++.+ +++++ .<+++ [->-- -<]>- -.+++ +++.< |
在以下网址中解密
https://www.splitbrain.org/services/ook
简单加密
1 | e6Z9i~]8R~U~QHE{RnY{QXg~QnQ{^XVlRXlp^XI5Q6Q6SKY8jUAA |
凯撒,用python跑一下
1 | str = "e6Z9i~]8R~U~QHE{RnY{QXg~QnQ{^XVlRXlp^XI5Q6Q6SKY8jUAA" |
a2V5ezY4NzQzMDAwNjUwMTczMjMwZTRhNThlZTE1M2M2OGU4fQ==
base64解码得到flag
散乱的密文
lf5{ag024c483549d7fd@@1}
一张纸条上凌乱的写着2 1 6 5 3 4
| 2 | 1 | 6 | 5 | 3 | 4 |
|---|---|---|---|---|---|
| l | f | 5 | { | a | g |
| 0 | 2 | 4 | c | 4 | 8 |
| 3 | 5 | 4 | 9 | d | 7 |
| f | d | @ | @ | 1 | } |
按照顺序读下来f25dl03fa4d1g87}{c9@544@
栅栏解密得到flag{52048c453d794df1}@@,格式flag{},去掉@@
凯撒部长的奖励
凯撒密码,MSW=SYC,词频分析
一段base64
使用编码工具Converter,将文本内容复制进去
按照以下次序解码base64、Unescape、Hex to Text、Unescape(只要括号内的参数)、Dec to Text、Decode HTML。最后得到Unicode编码:
1 | flag%7Bctf_tfc201717qwe%7D |
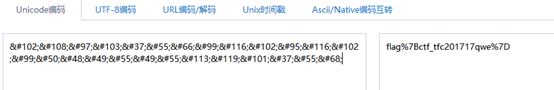
最后url解码得到flag(手动解码*^▽^*:”%7B”=”{“,”%7D”=”}”)
.!?
1 | ..... ..... ..... ..... !?!!. ?.... ..... ..... ..... .?.?! .?... .!... |
Ook短加密,解密地址https://www.splitbrain.org/services/ook
+[]-
1 | +++++ +++++ [->++ +++++ +++<] >++.+ +++++ .<+++ [->-- -<]>- -.+++ +++.< |
在以下网址中解密
https://www.splitbrain.org/services/ook
突然天上一道雷电
gndk€rlqhmtkwwp}z
变异凯撒,gndk=flag
1 | list = 'gndk€rlqhmtkwwp}z' |
托马斯.杰斐逊
1 | 1: <ZWAXJGDLUBVIQHKYPNTCRMOSFE < |
看了下王心慰的博客了解了下思路
先根据秘钥所提供的行号重新排序
1 | KPBELNACZDTRXMJQOYHGVSFUWI |
然后将密文的字母移动到第一列
1 | HGVSFUWIKPBELNACZDTRXMJQOY |
用脚本将每一列遍历出来,并找到特殊的句子即为flag
1 | a ="""HGVSFUWIKPBELNACZDTRXMJQOY |
通解
这是2017 ISCC write up basic的Wheel Cipher,与Bugku这题类似
1 | list1 = """因为key的关系,所以这一行换行很重要 |
zip伪加密
伪加密参考:https://blog.csdn.net/pdsu161530247/article/details/73612910
用winhex打开flag.zip,09改成00,保存即可。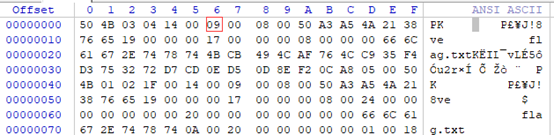
告诉你个秘密(ISCCCTF)
1 | 636A56355279427363446C4A49454A7154534230526D6843 |
HEX转ASCII
1 | cjV5RyBscDlJIEJqTSB0RmhCVDZ1aCB5N2lKIFFzWiBiaE0g |
base64解码
1 | r5yG lp9I BjM tFhB T6uh y7iJ QsZ bhM |
注意键盘上的位置,r5yG中间是t,以此类推答案就是tongyuan,
注意flag格式需要大写
这不是MD5
16进制转字符串
贝斯家族
贝斯==base,家族应该不是64,其他类型
试来试去,base91解码成功:Base91编码
富强民主
Python(N1CTF)
开局得到两个脚本,需要去逆解。
1 | from N1ES import N1ES |
1 | # -*- coding: utf-8 -*- |
加密过程和round_add都是可逆的,直接在源码文件中加入解密用代码如下:
1 | def re_round_add(a, b): |
然后修改challenge.py运行直接得到flag
1 | from N1ES import N1ES |
非预期解
1 | from N1ES import N1ES |
来自宇宙的信号
银河战队出击
flag格式 flag{字母小写}
对照密码表得到flag,参考百度百科:标准银河字母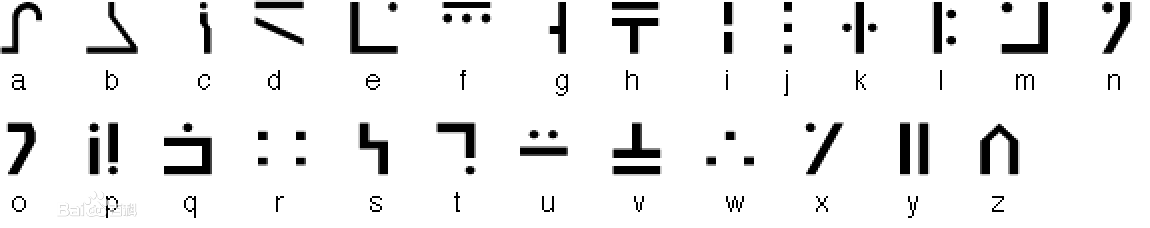
easy_crypto
一看0和1以为是进制转换,但仔细观察发现长度不对,感觉更像是摩斯电码,于是用代码替换下
1 | a='0010 0100 01 110 1111011 11 11111 010 000 0 001101 1010 111 100 0 001101 01111 000 001101 00 10 1 0 010 0 000 1 01111 10 11110 101011 1111101' |
其中一种解码后得到flag
进制转换
一堆不同进制的数值,猜测是转成16进制再转成字符串
1 | import binascii |
affine
放射函数,在实验吧做过类似题目
1 | list = 'abcdefghijklmnopqrstuvwxyz' |
Crack it
使用kali下的John the Ripper工具破解密码
1 | root@kali:~/Desktop# john --wordlist=/usr/share/john/password.lst shadow |
rsa
一看n、e、enc那么长,估计是Wiener’s Attack
使用rsa-wiener-attack脚本破解,这里需要修改下主函数↓
1 | if __name__ == "__main__": |