实验吧隐写题writeup
Fonts 这题主要考察word隐藏文字,在文件->选项->显示中勾选隐藏文字,即可得到flag
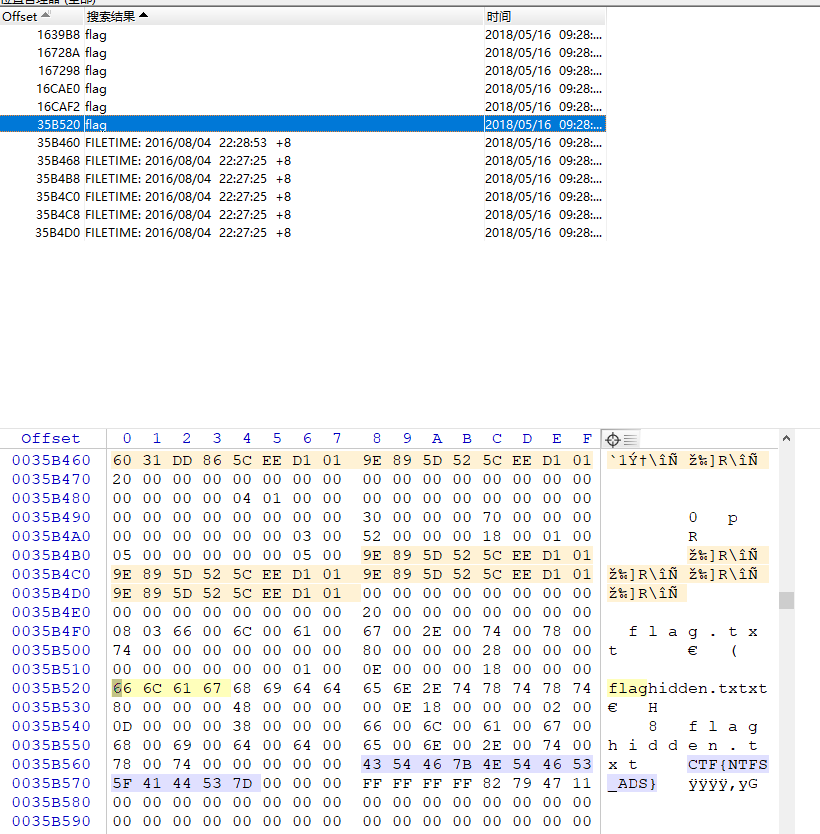
流 Winhex大法简单粗暴
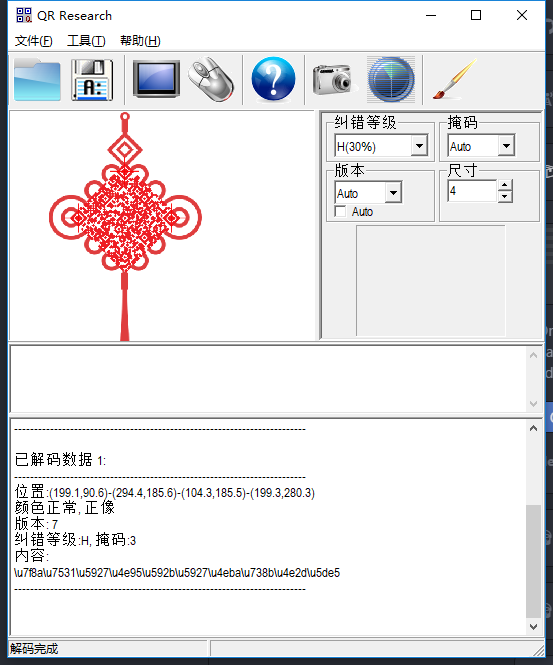
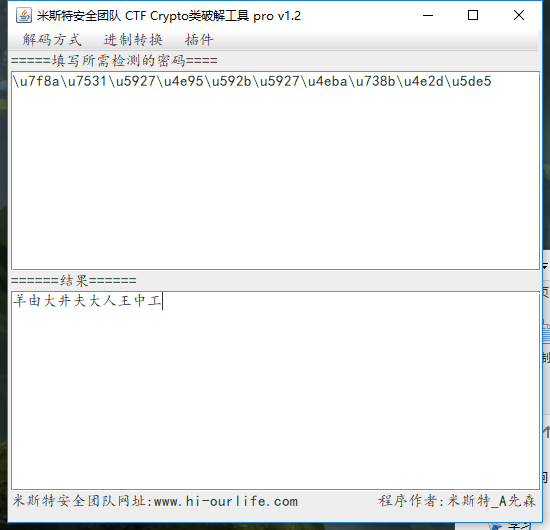
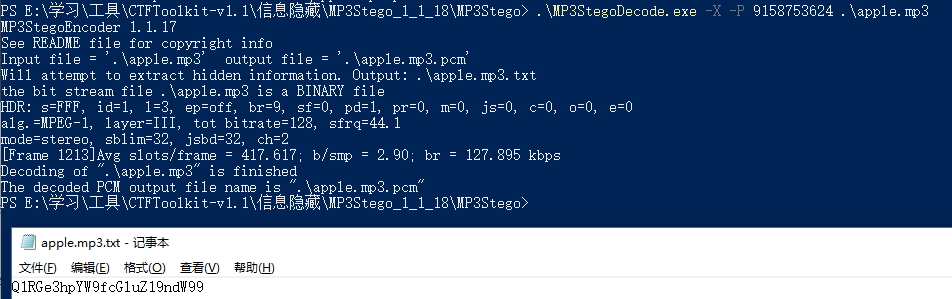
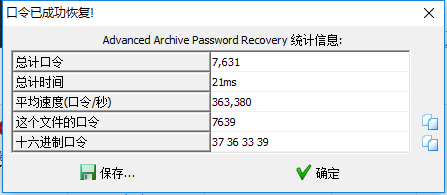
小苹果 1.先扫码当铺密码 解密
4.mp3解密
1 MP3StegoDecode.exe -X -P 9158753624 .\apple.mp3
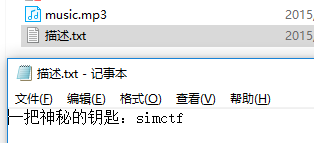
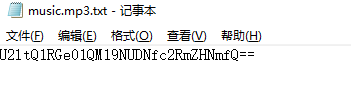
女神又和大家见面了 一张小姐姐的照片,用winhex打开发现有rar文件头,解压出来一个MP3文件和提示
1 MP3StegoDecode.exe -X -P simctf .\music.mp3
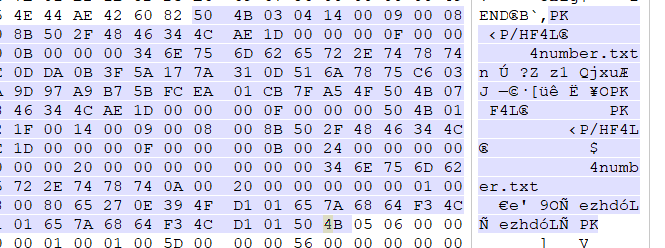
复杂的QR_code 用winhex打开可以看到zip文件头
1 2 3 4 5 6 7 root@kali:~/Desktop DECIMAL HEXADECIMAL DESCRIPTION -------------------------------------------------------------------------------- 0 0x0 PNG image, 280 x 280, 1-bit colormap, non-interlaced 471 0x1D7 Zip archive data, encrypted at least v2.0 to extract, compressed size: 29, uncompressed size: 15, name: 4number.txt 650 0x28A End of Zip archive
提示4位数字,爆破一下,拿到flag
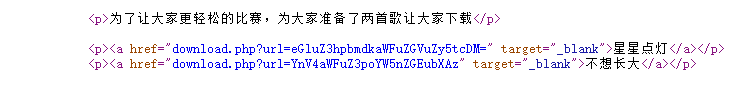
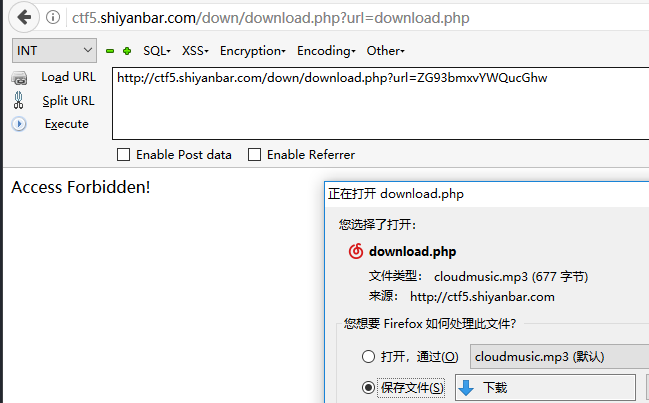
听会歌吧 右键查看源代码,发现url后门是base64编码的文件名
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 <\?php error_reporting(0 ); include ("hereiskey.php" );$url=base64_decode($_GET[url]); if ( $url=="hereiskey.php" || $url=="buxiangzhangda.mp3" || $url=="xingxingdiandeng.mp3" || $url=="download.php" ){ $file_size = filesize($url); header ( "Pragma: public" ); header ( "Cache-Control: must-revalidate, post-check=0, pre-check=0" ); header ( "Cache-Control: private" , false ); header ( "Content-Transfer-Encoding: binary" ); header ( "Content-Type:audio/mpeg MP3" ); header ( "Content-Length: " . $file_size); header ( "Content-Disposition: attachment; filename=" .$url); echo (file_get_contents($url)); exit ; } else { echo "Access Forbidden!" ; } ?>
同样方法将hereiskey.php下载下来得到flag
SB!SB!SB! StegSolve打开找到二维码
LSB lsb隐写,使用wbStego4.3open解码